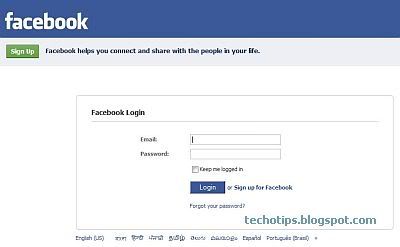
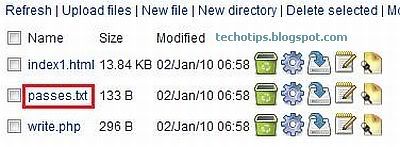
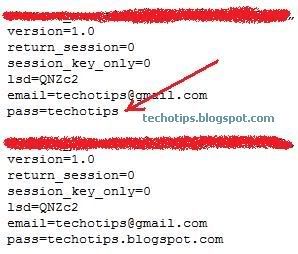
These are Top 20 Hacking Tools, the list is exhaustive, this are a few to name.
The “Nessus” Project aims to provide to the internet community a free, powerful, up-to-date and easy to use remote security scanner for Linux, BSD, Solaris, and other flavors of Unix.
Ethereal is a free network protocol analyzer for Unix and Windows. Ethereal has several powerful features, including a rich display filter language and the ability to view the reconstructed stream of a TCP session.
Snort is an open source network intrusion detection system, capable of performing real-time traffic analysis and packet logging on IP networks.
Netcat has been dubbed the network swiss army knife. It is a simple Unix utility which reads and writes data across
network connections, using TCP or UDP protocol
TCPdump is the most used network sniffer/analyzer for UNIX.
TCPTrace analyzes the dump file format generated by TCPdump and other applications.
Hping is a command-line oriented TCP/IP packet assembler/analyzer, kind of like the “ping” program (but with a lot of extensions).
DNSiff is a collection of tools for network auditing and penetration testing. dsniff, filesnarf, mailsnarf, msgsnarf, urlsnarf, and webspy passively monitor a network for interesting data (passwords, e-mail, files, etc.).
GFI LANguard Network Security Scanner (N.S.S.) automatically scans your entire network, IP by IP, and plays the devil’s advocate alerting you to security vulnerabilities.
>Ettercap is a multipurpose sniffer/interceptor/logger for switched LAN. It supports active and passive dissection of many protocols (even ciphered ones)and includes many feature for network and host analysis.
Nikto is an Open Source (GPL) web server
scanner which performs comprehensive tests against web servers for multiple items, including over 2500 potentially dangerous files/CGIs, versions on over 375 servers, and version specific problems on over 230 servers.
John the Ripper is a fast password cracker, currently available for many flavors of Unix.
OpenSSH is a FREE version of the SSH protocol suite of network connectivity tools, which encrypts all traffic (including passwords) to effectively eliminate eavesdropping, connection hijacking, and other network-level attacks.
Tripwire is a tool that can be used for data and program integrity assurance.
Kismet is an 802.11 wireless network sniffer – this is different from a normal network sniffer (such as Ethereal or tcpdump) because it separates and identifies different wireless networks in the area.
NetFilter and iptables are the framework inside the Linux 2.4.x kernel which enables packet filtering, network address translation (NAT) and other packetmangling.
IP Filter is a software package that can be used to provide network address translation (NAT) or firewall services.
OpenBSD Packet Filter
fport identifys all open TCP/IP and UDP ports and maps them to the owning application.
SAINT network vulnerability assessment scanner detects vulnerabilities in your network’s security before they can be exploited.
OpenPGP is a non-proprietary protocol for encrypting email using public key cryptography. It is based on PGP as originally developed by Phil Zimmermann.